Software industry has become an increasingly popular area with the recent advancements in technologies. More and more people have been seeking employment in this sector which offers several benefits including a wide variety of job opportunities, rapid promotion potential, flexible working hours, handsome wages, etc.
Structured as a highly non-transparent and corruption-prone entity, FETO has been one of the many terrorist organizations to discover the rich potential and the exploitable opportunities the software industry offered.
We have been observing a growing trend with FETO in directing its members, both within Turkey who seek to leave the country and those based in other countries, to seek employment in this particular industry that emerged as a relatively new line of business in need of educated and experienced manpower.
Accordingly, we have identified that FETO established several tech companies in a number of countries in the span of the last couple of years which allegedly offered online or in-person software trainings. The companies include the following:
- Cydeo (Cybertech) (Virginia, USA – FETO member Kuzzat ALTAY)
- Hacker Academy, (United Kingdom)
- Cybernow Labs (USA)
- NormShield Cyber Risk Scorecard
- Black Kite (USA)
- Keepnet Labs (United Kingdom)
- Clarusway (USA)
- NioyaTech LLC (USA)
People interested in the training including FETO member TAF (Turkish Armed Forces) and TNP (Turkish National Police) personnel must be vouched for by an acknowledged fellow FETO member who would put in a good word for them as eligible for the training: the main rule to be admitted in the training would be a recommendation by another FETO member. FETO member trainees receive a certificate of ‘Software Expert’ on different software languages at the end of the course.
Once the training is completed, a curriculum vitae is created for the graduates with the names of the course instructors or previous trainees portrayed as their purported ‘references’. The fake CVs are enriched with fabricated documents falsely attesting to 3-4 years of employment history depending on the level of the trainee. Providing ‘the so-called graduates who had undergone non-proficient trainings’ fraudulently-created qualifications such as former employment at fictitious companies or forged CVs, these companies offer their successful trainees shady jobs, preying on their professional incompetence/incapacity stemming from an actual lack of education, training and experience and thus, leaving them no other option than being dependent on FETO. US-based Cydeo (Cybertech) with its managing director FETO member Kuzzat ALTAY is the most popular software company highly preferred by the group members.
Cydeo guarantees employment upon completion of the training though it is contingent upon a legal undertaking obliging the graduates to sign a contract which legally bounds them to allocate a portion of their salary to the company every month. This is but a slightly different version of ‘himmah’ (charity), a FETO legacy requiring the FETO member government employees to earmark a portion of their salaries for the group. FETO is as steadfast as ever in forcing its members to fulfill such legacy requirements that are as old as its history.
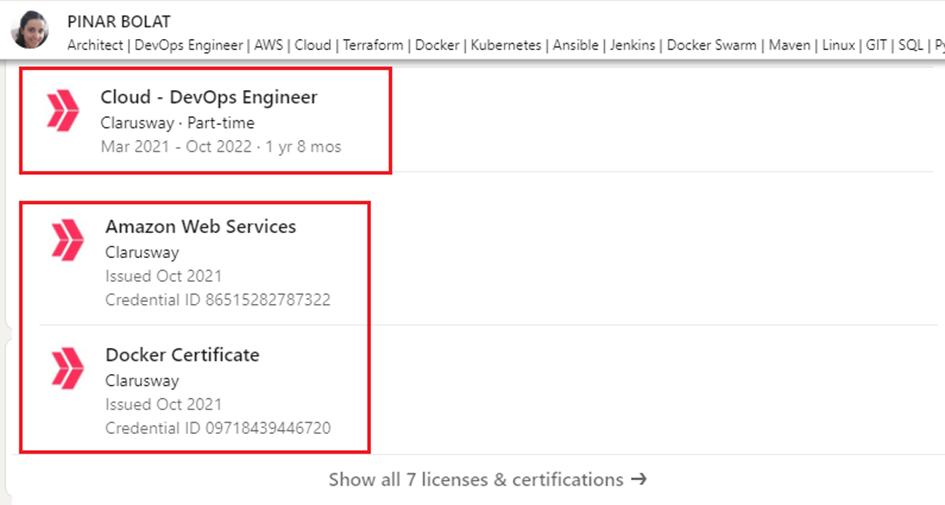
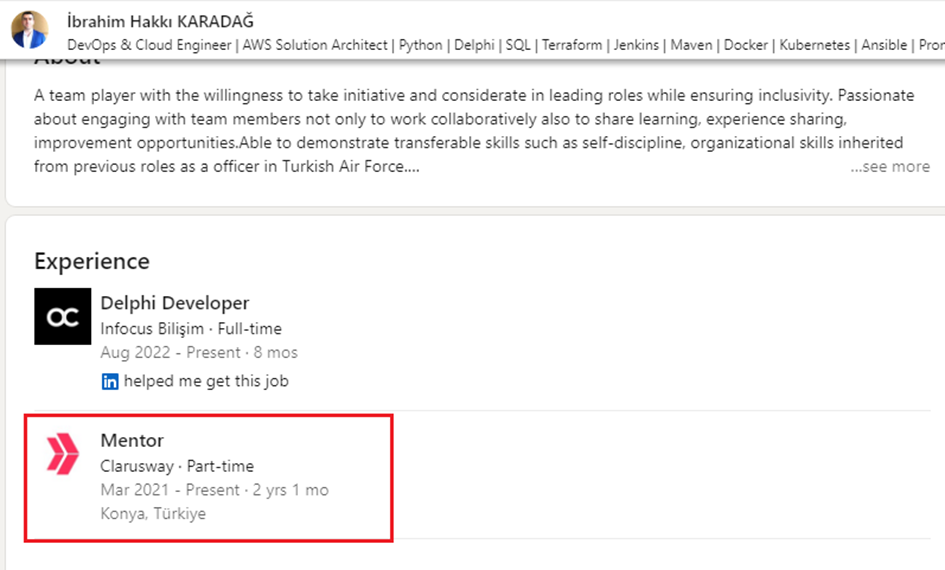
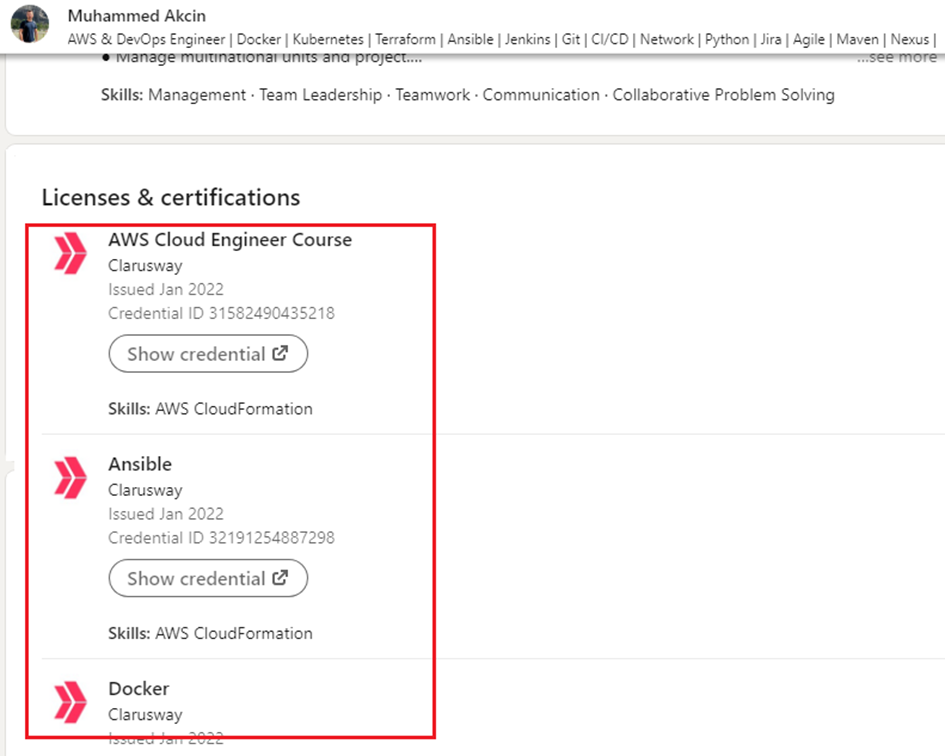
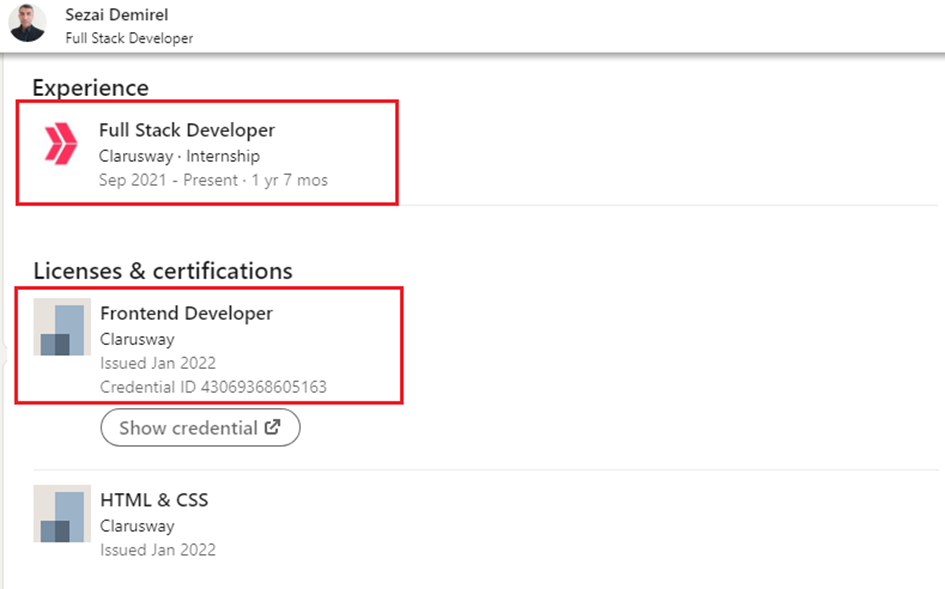
The FETO companies offering trainings are further supported by another group of front companies that are created with the sole purpose of acting as references to vouch for the potential graduates. The most renowned are Clarusway and NioyaTech LLC. Almost all of those trained by the US-based Clarusway online training company are Turkish FETO members who are not ‘just receiving training’ but also working at the company or volunteering as training instructors. FETO members pass sham tests at Clarusway and are granted certificates. The price for the Clarusway training varies between USD 10,000-15,000. The very high fees are an attempt at discouraging non-members from applying for the courses and laundering money through members. The almost exact same LinkedIn profiles of FETO members all of which advertise the Clarusway as the company where they received their training and offered employment are the telltale signs of the FETO strategy.
This report should demonstrate the magnitude of the danger FETO poses in the software industry. Not only the group is generating income in the form of training fees for software courses and poaching chunks of salaries –‘himmah’– from its members who found employment but also creating job opportunities for its fugitive members outside Turkey by means of providing forged certificates and CVs.
The foregoing activities which are of organized crime nature should not be permitted if the global cyber security is to be effectively protected.